
GET READY TO HACK
We simulate sponsored attacks
RED TEAM
Our Red Team has the purpose to simulate an unauthorized access to corporate systems through a sponsored external attack, a classic penetration, long-term persistence, corporate system privilege escalation, and even alteration and theft of business strategical information. The Red Team periodically reports on findings and taken and future actions to a select group of people as directed by the client, so it can always stay updated on the campaign progress, as well as first-hand information on the defending team (Blue Team) performance.
Continuous evaluation of the security posture
Continuous testing and permanent alerting of SOC monitoring service
Staff training on realistic offensive scenario
Catalog of tests on different attack vectors
Strategy development through kill chain controls
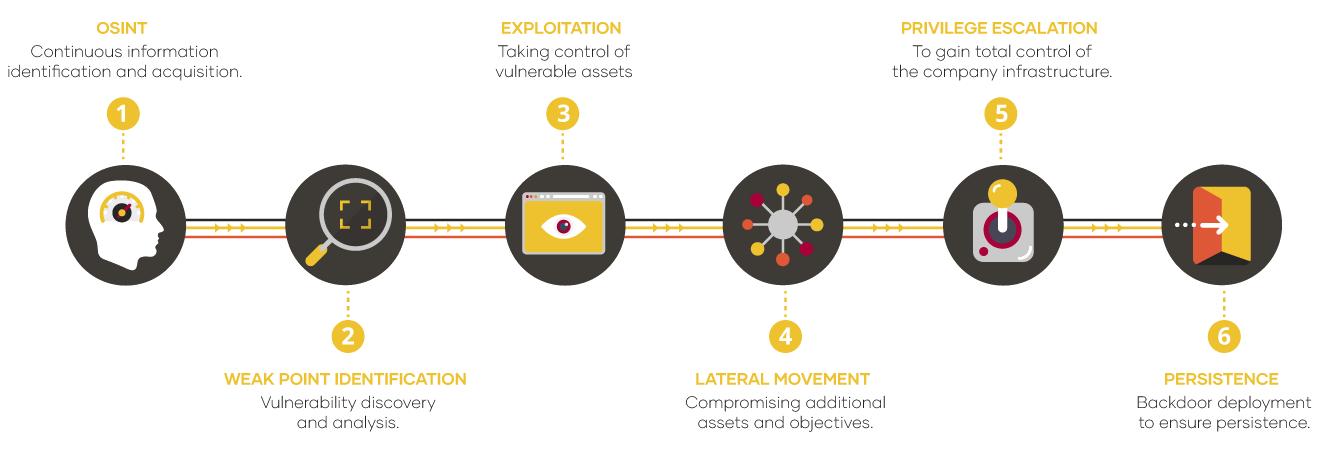
1ª PHASE
Intrusion
Initial compromise from the perimeter. This task is continuous throughout the service to discover new attack vectors.
2ª PHASE
Attack scenarios
Setup and execution of different attack based on scenarios (insider, corporate laptop theft, suppliers...).
3ª PHASE
Targeted attacks
Identification and selection of targeted attacks against critical assets which may include controlled infection through APT.
4ª PHASE
Maturity
Analysis of results and development of strategies for mitigation and operational improvements.
CAPABILITIES
RED TEAM LABS
From 0-day to exploit
Research and discover of new vulnerabilities (0-day) in company technologies.
Development of advanced tools, exploits and custom malware to simulate the TTPs used by different threat actors (from standard attacker to APT groups).


RED TEAM INTEL
OSINT
Asset discovery, technology fingerprinting and information leakage detection.
Continuous task throughout the service to detect new assets or leaks that may lead to new attack vectors.
New findings are used to feed back the discovery process.